
gOVERNANCE, RISK AND COMPLIANCE (gRC)
The Best Security is a Proactive Security
Take advantage of our risk, compliance and security service to understand and manage your risk, achieve and maintain compliance, make certain everyone is trained to spot a cyber-attack, monitor vulnerabilities and Dark Web analysis.
Form an defensive line of prevention that stops an attack before it strikes.
We Provide You With:
Risk Assessments
Technical Assessments
Vulnerability Assessments
Penetration Testing
Simulated Phishing
Remediation Recommendations & Plans
Employee Training
Policy Management
Risk Management
Incident Reporting
Dark Web Monitoring
Web AD Integration
ARE YOU COMPLIANT?
Your Business Could Be At Risk:
Is Your Business Ready For The DoD’s CMMC Deadline?
Get A FREE 10-Point CMMC Action Plan With A Certified Assessor To Find Out Now:
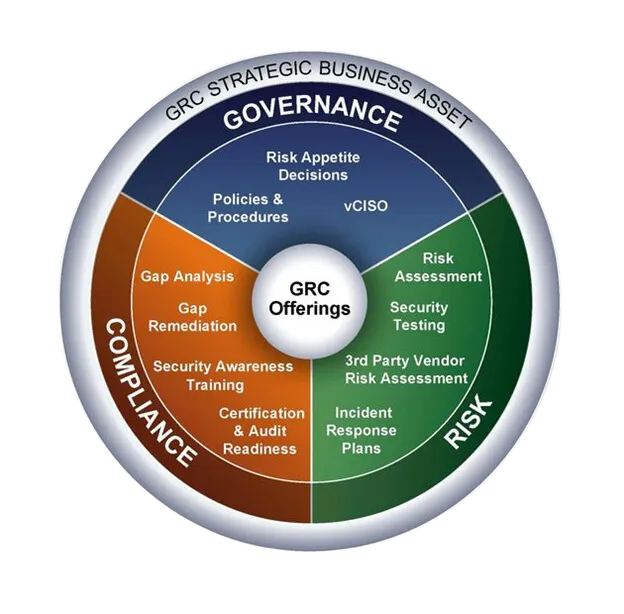
THE THREE PILLARS OF GRC
Governance
Stealth- ISS provides services like CISO-as-a-Service (CISOaaS), where it offers organizations executive-level guidance on establishing and managing their cybersecurity program. This typically includes creating policies and procedures, setting up a governance structure, and developing a strategic plan for information security.
Risk
Stealth- ISS team helps organizations identify and manage their cybersecurity risks. This can involve conducting risk assessments, penetration testing, and vulnerability assessments to identify potential threats and vulnerabilities. We also provide guidance on implementing risk mitigation strategies and improving the organization's overall cybersecurity posture.
Compliance
Stealth- ISS offers a range of services to help organizations comply with a wide array of regulatory and industry standards, such as NIST Cybersecurity Framework, ISO 27001, PCI DSS, HIPAA, and others. We can help organizations understand their compliance obligations, implement necessary controls, and prepare for audits.
BY KEEPING YOUR KEY BUSINESS OBJECTIVES IN MIND, WE HELP YOU ACHIEVE A SECURE ENVIRONMENT AND COMPLIANCE EFFICIENTLY.
WHY CHOOSE US?
Our comprehensive approach forms a preventive barrier between your business and potential cyber-attacks.
From NIST, CMMC, HIPAA to PCI to GDPR, compliance regulations are constantly changing. Stealth-ISS Governance, Risk and Compliance consultants help you comply with prevailing regulatory requirements, respond to situations of noncompliance, and improved your processes around information systems supporting GRC.
cOMPLIANCE ROADMAP AT A GLANCE:
PHASE 1
Understand Your
Regulatory Compliance
Start with the most important question – what regulatory compliance standards do you need to comply with? Every industry is different.
PHASE 2
Create a
Compliance Plan
Start with the basics – get a clear picture of who and what is involved with compliance.
PHASE 3
Identify
Existing Gaps
Identify all existing gaps you may have in the areas of people, process and technology.
PHASE 4
Put Your Planning in Motion
Put your plan in motion. Be sure that all involved diligently adhere to governance rules.
PHASE 5
Maintenance and Operations
Compliance isn’t static; regulations change. We make sure your organization stays current.
READY TO GET STARTED?

Schedule a meeting with one of our security experts and find out how Stealth-ISS' managed detection and response capabilities can help you.
Understanding GRC is a must for every organization. It's not just about preventing cyber-attacks but governing data, managing risks proactively, and ensuring compliance.
A robust GRC strategy means a resilient organization. And your organization's security is too important to leave to chance.
Get ahead, stay safe, and lead with confidence. Contact us today and we'll answer all your questions and help you meet all your existing regulatory requirements, remediate-non compliance issues, and enhance the efficiency of your business systems.

So, what are you waiting for?
Schedule a Meeting with One of Our Security Experts